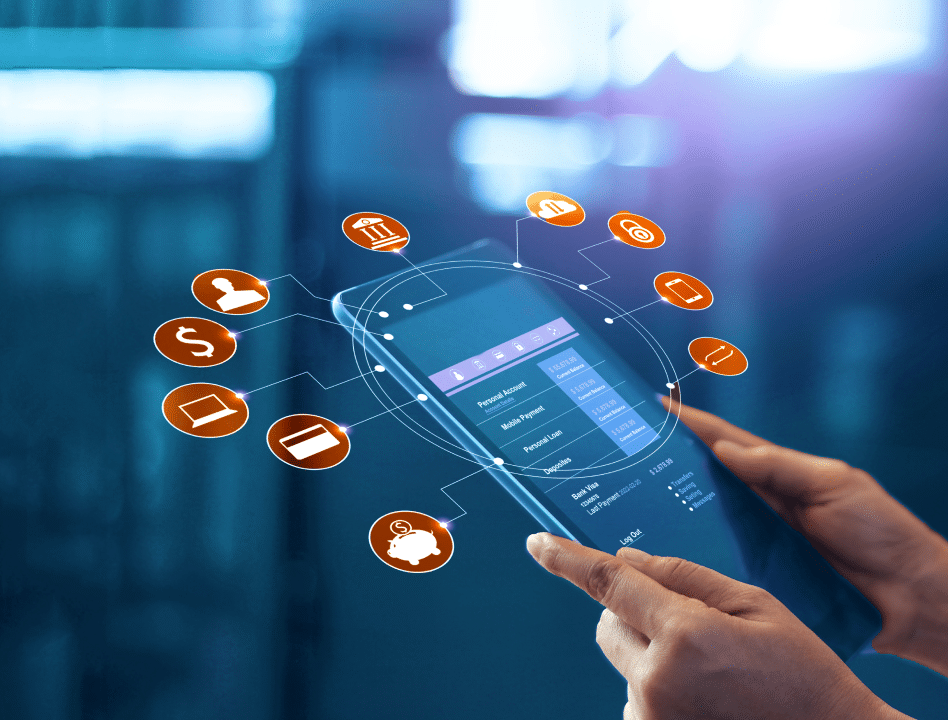
Digital transactions are the norm for many industries today, which means that the challenge of verifying identities accurately and securely has never been more critical. Ensuring that individuals are who they claim to be in the digital realm is not just a matter of trust; it’s a cornerstone of security and fraud prevention. With its intelligent use of AI technology like machine learning, Socure Document Verification is a robust, efficient tool for digital identity verification that protects against the massive threat of identity fraud.
ID verification online
Digital identity verification is an umbrella term encompassing various methods and tools used to authenticate individuals’ identities in the online realm, reflecting the evolving landscape of business and services conducted in the post-COVID digital world.
Two key examples of digital identity verification include:
- Passive digital identity verification systems verify users through passive indicators, including their online behaviors, device history and transaction patterns, without requiring active input.
- Digital ID verification involves the examination of digital documents and personal information provided by users to confirm their identity.
In an era where most transactions and interactions occur online, digital identity verification systems are pivotal in safeguarding businesses and users from fraud and identity theft.
What are the benefits of digital identity verification?
The benefits of digital identity verification are multifaceted, and platforms like Socure show you the best of what they have to offer. Socure offers an integrated end-to-end solution throughout the entire buyer’s journey, ensuring comprehensive identity verification rather than focusing on isolated aspects.
Unlike providers offering single-pillar ID verification, Socure’s approach covers the entire spectrum, from the initial prospect’s first interaction to onboarding, transactions, account changes, and account transfer phases. This holistic integration allows for continuous risk assessment, ensuring the safety of business transactions at every stage. Doing so enhances security, boosts efficiency, minimizes fraud, and bolsters customer trust, making it an indispensable tool in the modern business toolbox.
Socure’s end-to-end digital identity verification solution provides the following benefits.
- Enhanced security: Digital identity verification adds an extra layer of security by ensuring that individuals are who they claim to be. This helps prevent unauthorized access, identity theft, and fraud.
- Reduced fraud: With more robust identity verification measures in place, organizations can significantly reduce instances of fraud, such as account takeovers, fake accounts, and phishing attacks.
- Regulatory compliance: Many industries, such as financial services and healthcare, are subject to strict regulatory requirements for identity verification. Implementing robust digital identity solutions helps organizations comply with these regulations.
- Data privacy: While it may seem counterintuitive, proper digital identity verification can enhance data privacy by ensuring that personal information is only accessible by authorized individuals.
- Trust and reputation: Implementing strong identity verification measures can help build trust between businesses and customers and establish a reputable online presence.
Socure’s ID verification solution helped PrizePicks grow its member base by 1 million in 10 months. Explore the case study.
What are the different types of identity verification?
Multi-layered identity verification leverages a multi-tiered approach to deliver accurate, effective verification at each step of the buyer’s journey. For instance, progressive onboarding begins with a passive, low-touch verification check followed by a deeper check at onboarding. Understanding the different types of identity verification and their uses ensures a robust defense against identity fraud.
Identity verification can include:
- Socure Verify: A system that uses advanced machine learning to authenticate individuals and accurately detect identity fraud in real time.
- Document Verification: Document verification involves validating the authenticity of documents connected to a person’s identity which may include utility bills, business forms, or other related documents. This form of verification is typically combined with an ID verification to confirm an individual's identity.
- Identity Document Verification (ID Verification): In this case, ID verification refers to a specific ID document or credential that can be checked as the primary stage of ID verification and is followed up by biometric verification and liveness detection.
- Email verification: Ensures the accuracy, legitimacy, and risk factors associated with the email address provided during registration or account setup processes.
- Phone verification: Phone verification looks at the phone number to look for risky factors or previously associated fraud, prior to using that number to confirm the ownership of a phone number and its connection to an individual.
- Fraud checks: Fraud checks, like Sigma Identity Fraud, employ advanced algorithms and data analysis to detect suspicious activities and patterns indicative of identity fraud or fraudulent transactions.
- eCBSV: Electronic Consent-Based Social Security Number Verification (eCBSV) is a service that verifies Social Security numbers (SSNs) to prevent identity theft and fraud.
- Device and behavioral analytics: These analytics use data from user devices and behavior patterns to assess the legitimacy of user activities.
- Knowledge-Based Authentication (KBA): KBA systems include passwords, PINS, and personal identity questions, all of which can easily be hacked or guessed with social engineering. Going beyond KBA with better alternatives like Socure is safer for organizations and their customers.
Are there identity verification regulations?
There are several regulations and standards related to identity verification practices,each with specific requirements and purposes to ensure the security, integrity, and reliability of the identity verification process. Here's an overview of several key regulations and standards:
- NIST PAD Level 2: National Institute of Standards and Technology (NIST) Presentation Attack Detection (PAD) Level 2 certification focuses on liveness detection to thwart spoofing attacks. It is designed to differentiate between genuine users and fraudulent attempts using various tactics, such as 3D printers, masks, or dolls. Compliance with this standard ensures that identity verification methods can effectively distinguish between real users and impersonators, bolstering security.
- NIST IAL 2: NIST Identity Assurance Level 2 (IAL 2) is a standard for identity proofing that sets criteria for verifying an individual's identity. It involves multifactor authentication and rigorous identity validation processes. Complying with NIST IAL 2 ensures a higher level of confidence in the accuracy of the verified identity, making it essential for secure digital transactions.
- WCAG 2.1 Level AA: The Web Content Accessibility Guidelines (WCAG) 2.1 Level AA standard focuses on making digital content more accessible to individuals with disabilities, including those using mobile devices. Adherence to these standards is crucial to ensure that the verification process is user-friendly and accessible to all, enhancing the inclusivity and flexibility of digital identity verification.
- Soc2 Type 2: System and Organization Controls 2 (SOC 2) is a framework designed for service organizations to demonstrate their commitment to the security, availability, processing integrity, confidentiality, and privacy of customer data. Soc2 Type 2 certification ensures that organizations handling identity data maintain high levels of security and data protection throughout their operations.
- ISO Standards: International Organization for Standardization (ISO) standards encompass a wide range of criteria for various industries. In the context of identity verification, ISO standards relate to information security, data protection, and risk management.
Socure’s Predictive DocV Platform meets all industry security standards, including System and Organization Controls (SOC) 2 Type 2 mapped to HITRUST, and International Organization for Standardization (ISO) 27001, 27017, 27018, 27701, which enhances the ability to protect PII in accordance with applicable policies.
Other security standards that Socure meets include Anti-Money Laundering Directive 5 (AML 5) – designed to prevent money laundering and terrorist financing – and Customer Identification Program (CIP) – the component of AML regulations that require financial institutions to verify the identity of their customers before providing certain financial services.
Learn more about what Socure’s DocV solution can do for your organization’s security!